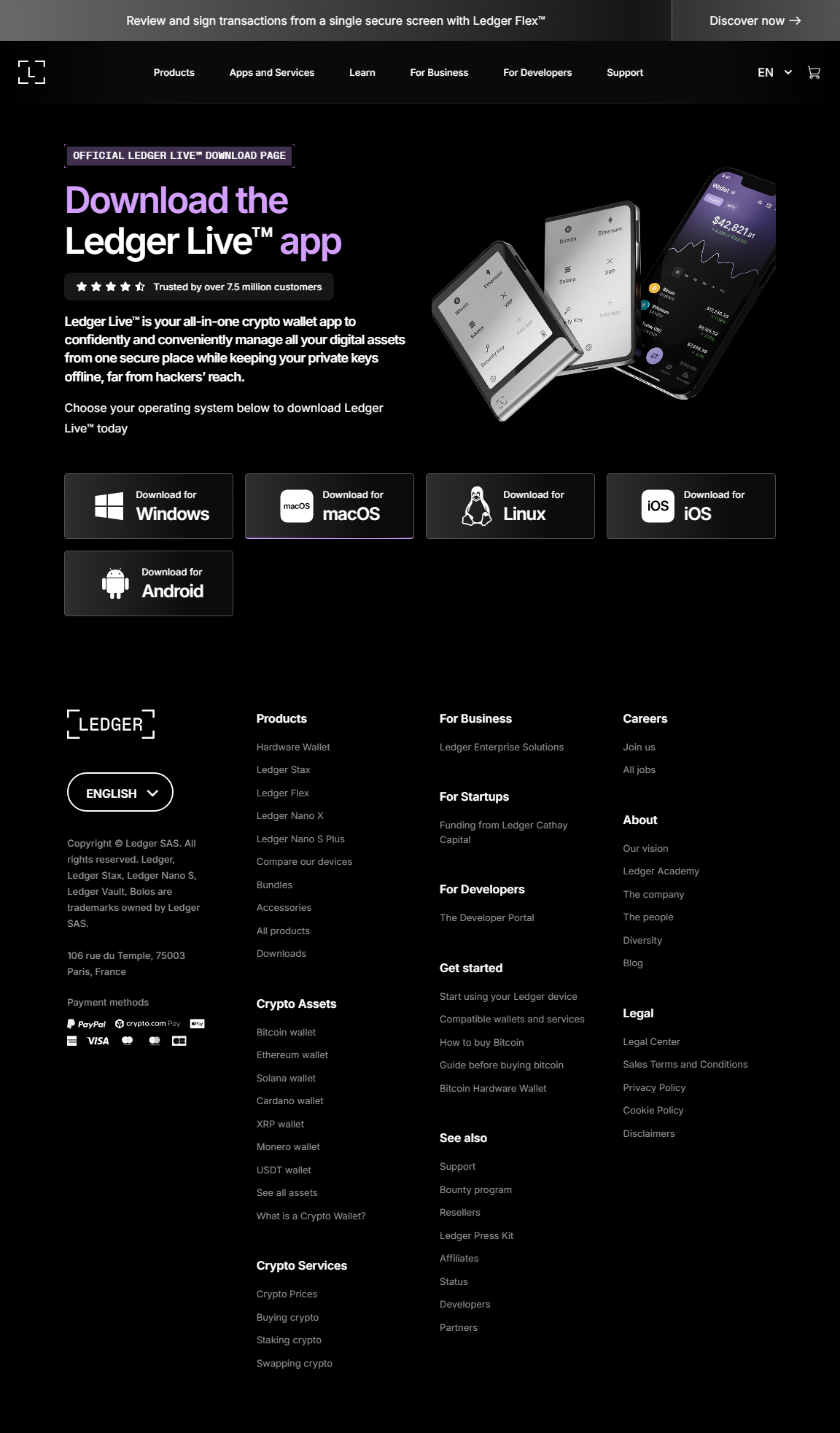
Mastering Ledger.com/start: Secure Your Crypto Like a Pro
A comprehensive guide to setting up your Ledger hardware wallet, understanding crypto security, and confidently managing digital assets from beginner to intermediate levels.
Why Use Ledger Wallets?
Cryptocurrency freedom comes with responsibility. Unlike traditional banks, losing access to your crypto can be irreversible. Ledger hardware wallets provide offline, ultra-secure storage for your private keys, reducing risks from hacks, malware, and phishing attacks.
Imagine your Ledger wallet as a digital vault—accessible only with your personal PIN and recovery phrase, safe even if your computer is compromised.
Highlight: Benefits of Ledger.com/start
- Offline storage of private keys ensures maximum security.
- Supports hundreds of cryptocurrencies including BTC, ETH, and stablecoins.
- Easy-to-use interface through Ledger Live software.
- Backup and recovery with a 24-word recovery phrase.
- Firmware updates keep your device protected against new threats.
Step-by-Step Setup: Ledger.com/start
Step 1: Visit the Official Start Page
Type Ledger.com/start into your browser to avoid phishing scams. This page will guide you through downloading Ledger Live and connecting your hardware wallet.
Step 2: Unbox Your Ledger Device
Check that your Ledger package is sealed and authentic. The device should come with a USB cable, recovery sheet, and the hardware itself. Authenticity is critical—never use a device with suspicious packaging.
Step 3: Install Ledger Live
Ledger Live is the software bridge between your device and your computer. Install it according to instructions. It allows you to manage multiple cryptocurrencies securely, check balances, and perform transactions.
Step 4: Initialize Your Device
Choose either Set up as new device or Restore from recovery phrase. Ledger will generate a 24-word recovery phrase—your master key. Store it safely offline; do not take photos or save digitally.
Step 5: Set a PIN
Choose a secure PIN for device access. Even if someone steals your hardware, the PIN prevents unauthorized access.
Step 6: Add Accounts and Manage Assets
Within Ledger Live, you can add accounts for Bitcoin, Ethereum, and other supported coins. Ledger Live allows sending, receiving, and portfolio tracking. Always double-check transaction addresses.
Essential Crypto Terms for Ledger Users
- Private Key: Secret access code for crypto assets.
- Public Address: Shareable wallet address to receive crypto.
- Seed Phrase: 24 words to recover your wallet if lost.
- Hardware Wallet: Offline device storing crypto keys securely.
- Hot Wallet: Internet-connected wallet, convenient but less secure.
- Cold Wallet: Offline storage, e.g., Ledger hardware wallet.
Ledger vs Other Wallets: At a Glance
| Feature | Ledger | Hot Wallet | Paper Wallet |
|---|---|---|---|
| Security | Very High (Offline) | Medium (Online) | High (Offline, fragile) |
| Ease of Use | High | Very High | Low |
| Backup & Recovery | Yes (Seed Phrase) | Yes (Software/Cloud) | No |
| Multi-Currency Support | Hundreds | Limited | Limited |
Pro Tips for Ledger.com/start Users
- Always download Ledger Live from the official site.
- Never share your 24-word recovery phrase digitally or online.
- Keep your firmware updated to maintain security against new threats.
- Consider a fireproof or secure storage for your recovery sheet.
- Verify addresses before sending crypto to avoid mistakes.
FAQs About Ledger.com/start
Q: Can I recover my crypto if my Ledger is lost?
A: Yes, using your 24-word seed phrase, you can restore your crypto on a new Ledger or compatible wallet.
Q: Does Ledger support mobile devices?
A: Yes, Ledger Live Mobile allows secure crypto management on Android and iOS devices, though full functionality may vary by device.
Q: Which cryptocurrencies are supported?
A: Ledger supports over 1800+ cryptocurrencies including Bitcoin, Ethereum, Ripple, and most ERC-20 tokens.
Conclusion
Ledger.com/start provides a secure, beginner-friendly gateway to managing cryptocurrencies safely. By following the setup steps, understanding crypto fundamentals, and implementing best security practices, both new and mid-level users can confidently protect and grow their digital assets. Remember, in crypto, your security is only as strong as your wallet and recovery practices.